In this POC we will integrate OpenLDAP with Pega Personal Edition 8.7
Demo Video:
Use case: How to Configure OpenLDAP with Pega 8.7
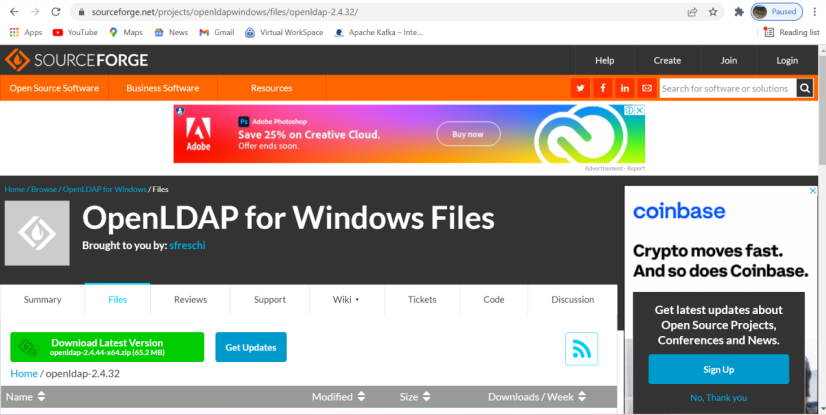
Download the software from
https://sourceforge.net/projects/openldapwindows/files/openldap-2.4.32/
Download in D:\OpenLDAP
Download OpenLDAPBrowser from
http://www.ldapbrowser.com/
in this folder ldapbrowser-4.5.19808.0-x64-eng
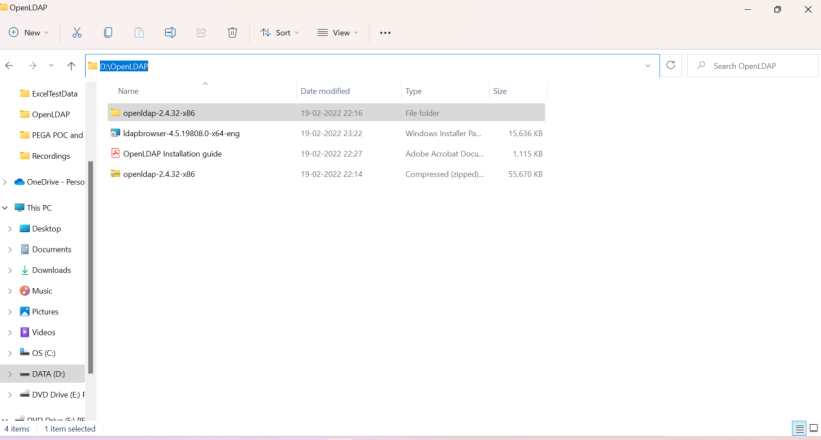
Unzip the folder openldap-2.4.32-x86
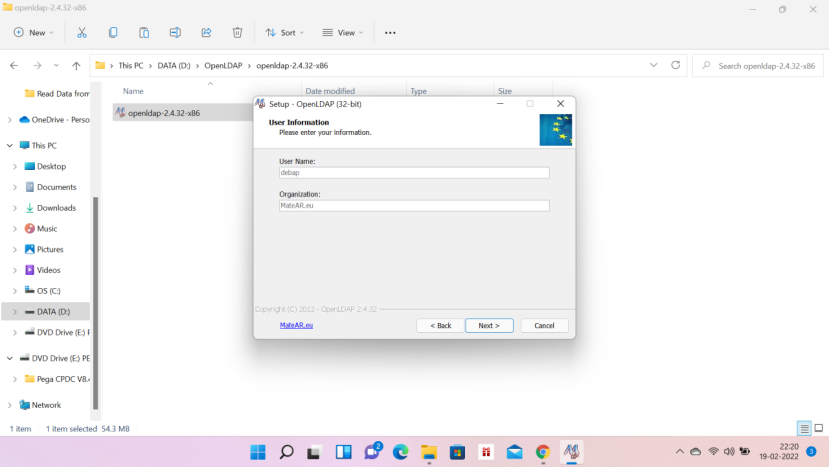
Now click the .exe file as below and start the installation. Installation folder will be D:\OpenLDAPInstall
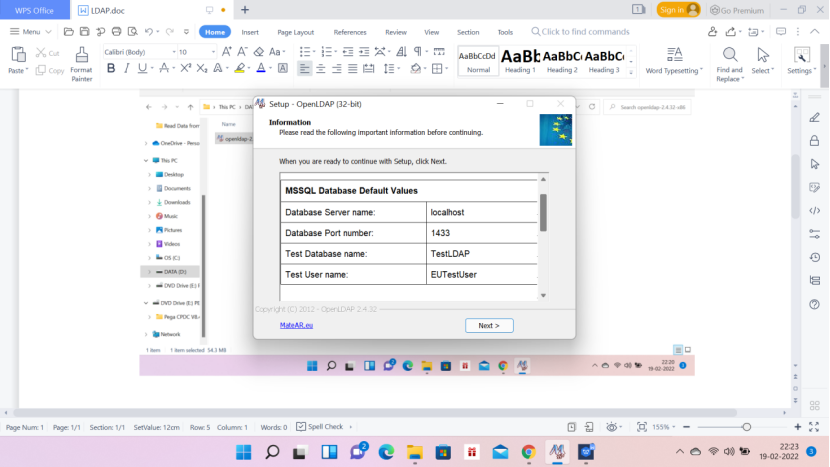
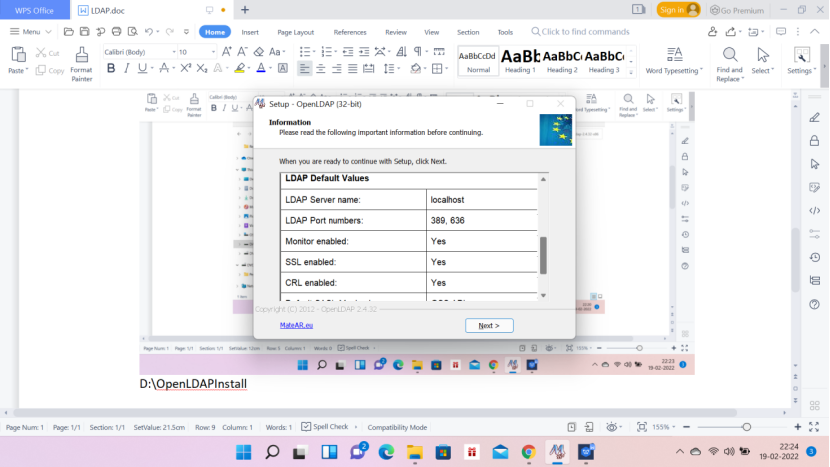
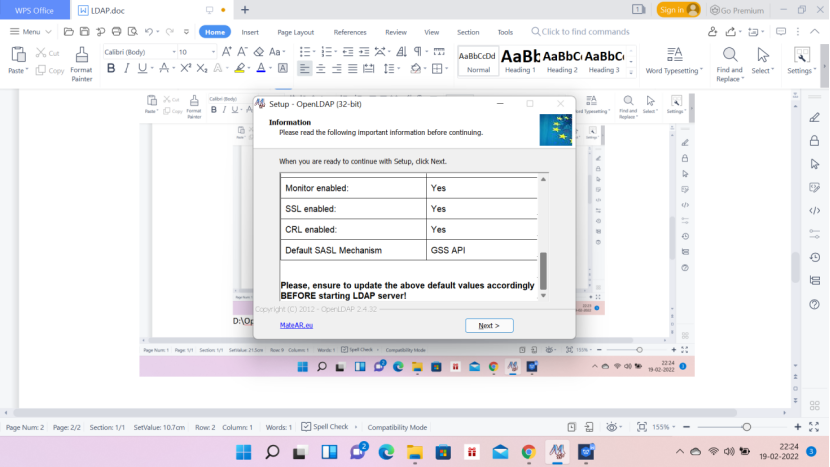
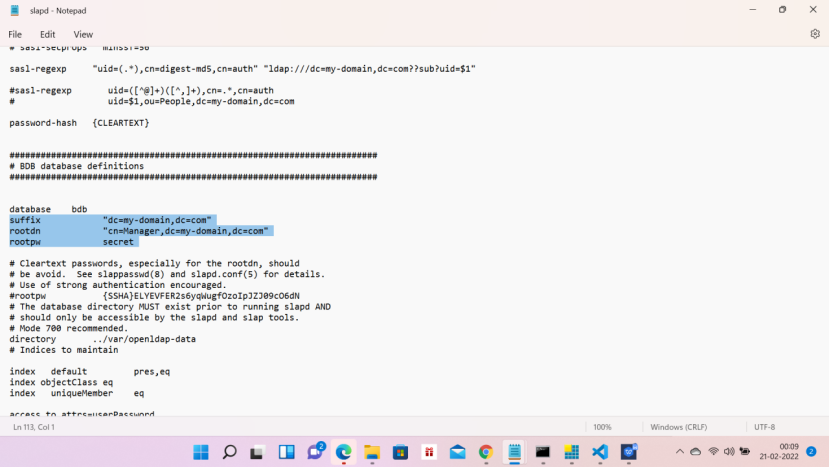
Update the slapd.conf file from D:\OpenLDAPInstall\etc\openldap. See the below lines.
suffix “dc=my-domain,dc=com”
rootdn “cn=Manager,dc=my-domain,dc=com”
rootpw secret
Note: Double check — there is a LDIF file with the same name.
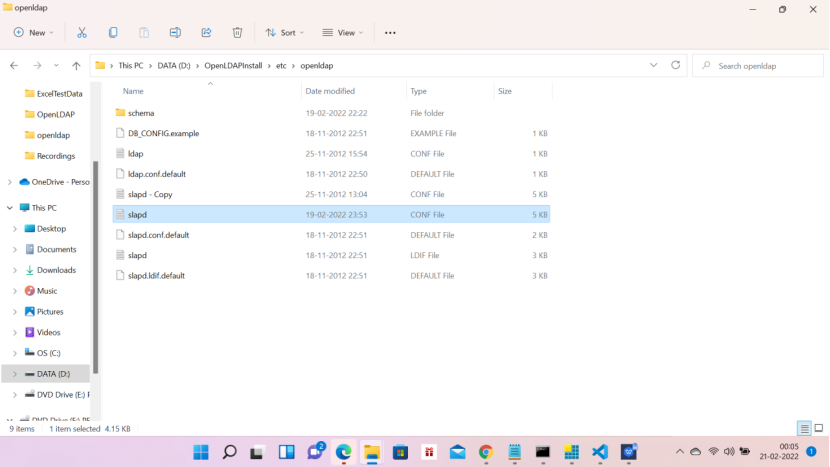
Create a LDIF file with the entries below for testing e.g. users-seri9.ldif from D:\OpenLDAPInstall\etc\ldif
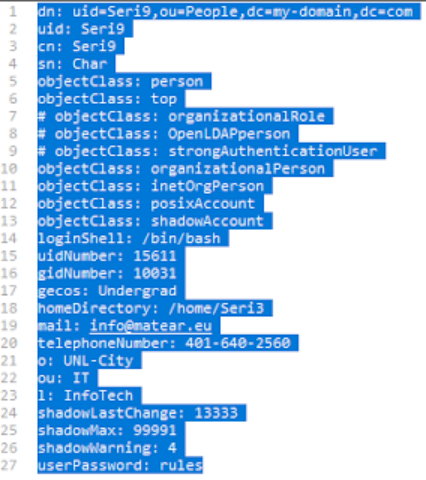
Create the file in notepad– users-seri9.ldif with the below entries
To start the OpenLDAP server:
Go to
Double click StartLDAP — it will start the server
It will look like as below
Now run the below commands
- D:\OpenLDAPInstall\bin>ldapmodify -a -v -D cn=Manager,dc=my-domain,dc=com -w secret -h localhost -p 389 -P 3 -x -f D:\OpenLDAPInstall\etc\ldif\base.ldif (To modify the pwd for a file:base.ldif)
- D:\OpenLDAPInstall\bin>ldapadd -h localhost -p 389 -D “cn=Manager,dc=my-domain,dc=com” -W -f D:\OpenLDAPInstall\etc\ldif\users-seri9.ldif (To add a new user in the LDAP server)
- D:\OpenLDAPInstall\bin>ldappasswd -H ldap://localhost -x -D “cn=Manager,dc=my-domain,dc=com” -W -S “uid=Seri9,ou=People,dc=my-domain,dc=com” (To update the pwd for a user)
- D:\OpenLDAPInstall\bin>ldapdelete -v “uid=ModelUser,ou=People,dc=my-domain,dc=com” -D “cn=Manager,dc=my-domain,dc=com” -W (To delete a user in the LDAP server)
- D:\OpenLDAPInstall\bin>ldapsearch -x -b “ou=People,dc=my-domain,dc=com” -H ldap://localhost (To search the LDAP server and will give all the details)
- D:\OpenLDAPInstall\bin>ldapsearch -x -b “ou=People,dc=my-domain,dc=com” “objectclass=*” (To search the LDAP server and will give all the details)
Now download OpenLDAP browser in D:\OpenLDAP
Double click ldapbrowser-4.5.19808.0-x64-eng
Start the installation in the folder, D:\OpenLDAPBrowser
Installation is simple– so did not take any screen shots
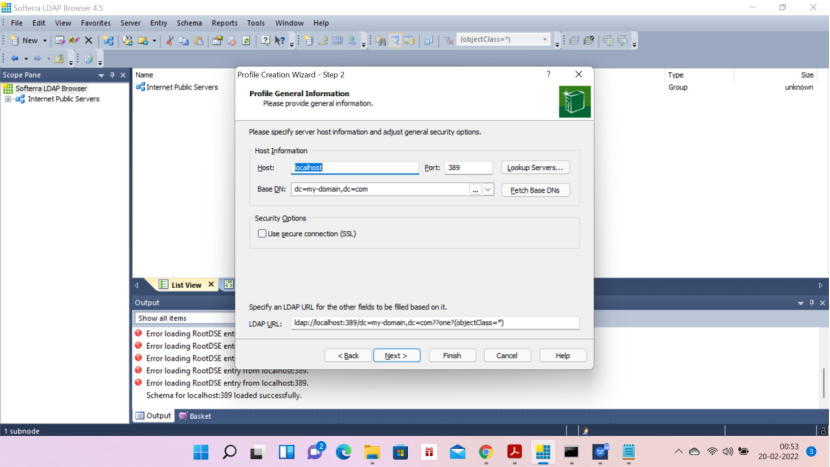
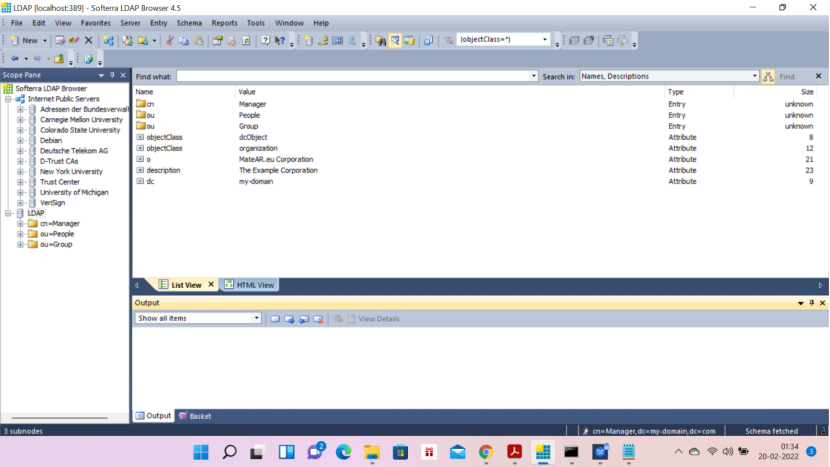
Now in the browser—right click on Softerra LDAP Browser — Give the name as LDAP–Click next–you will get the below screen
Click FetchBase DNs — then data will be populated
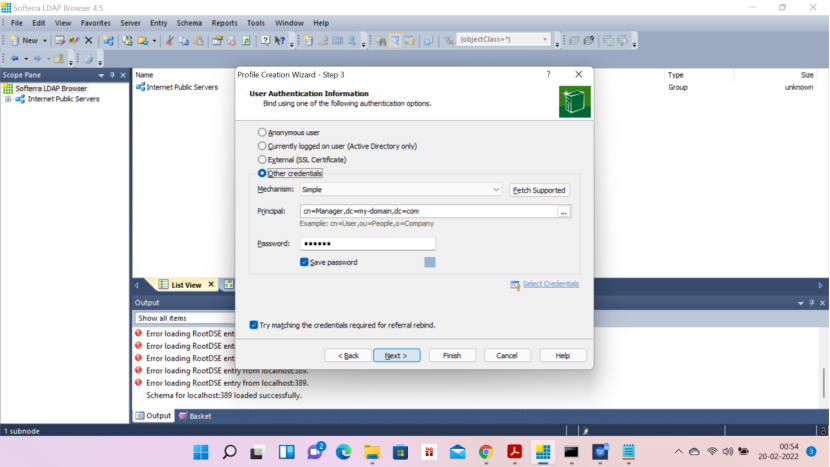
Now the below screen: Principal: type cn—remaining thing will be populated
Password- secret
In the next screen — there will be object in the 1st field — just click next and you will get
Now login to Pega 8.7 – with your credentials 🙂
Records – SysAdmin – Authentication Service
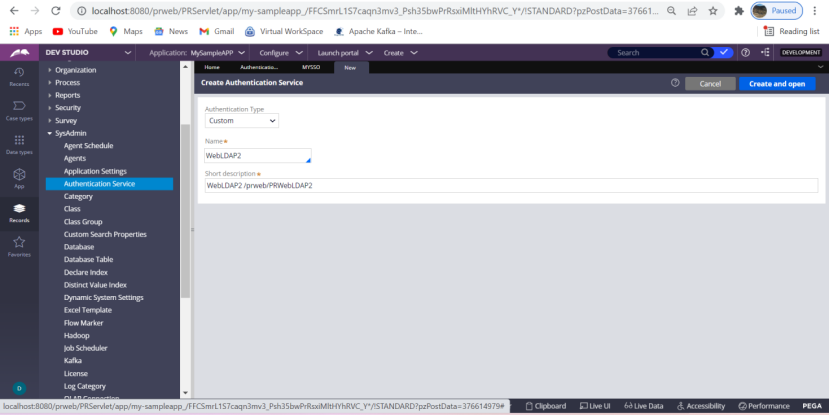
Authentication type Custom
Name: WebLDAP2
Short description will populate automatically
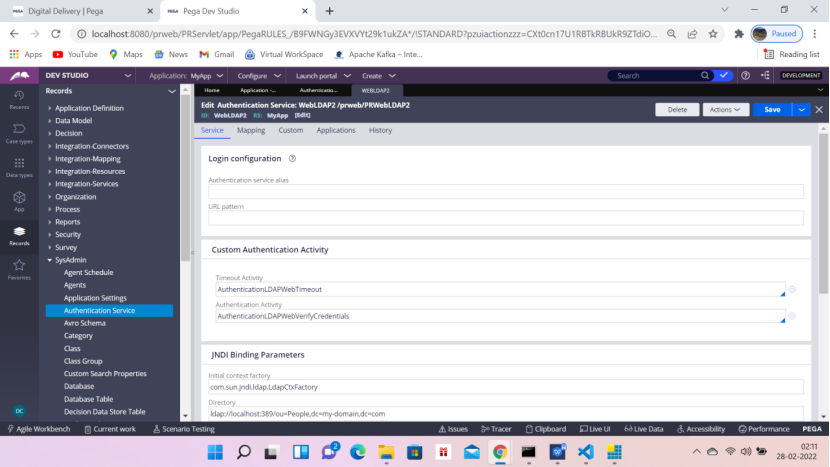
Enter the following activities
AuthenticationLDAPWebTimeout
AuthenticationLDAPWebVerifyCredentials
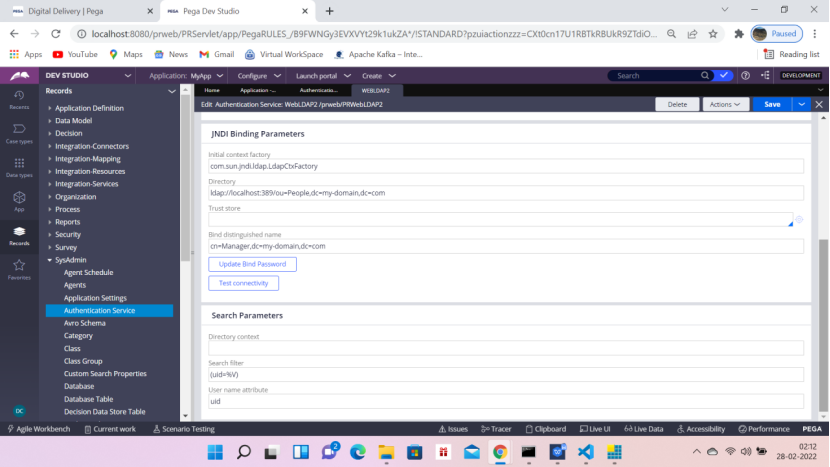
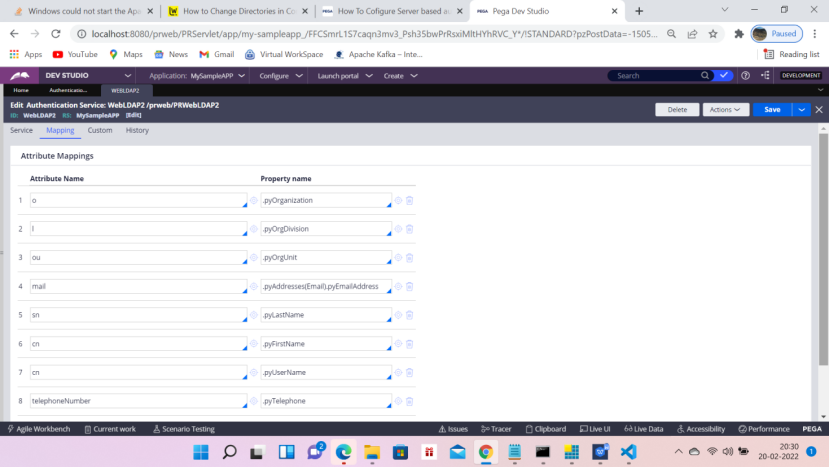
Click Test Connectivity
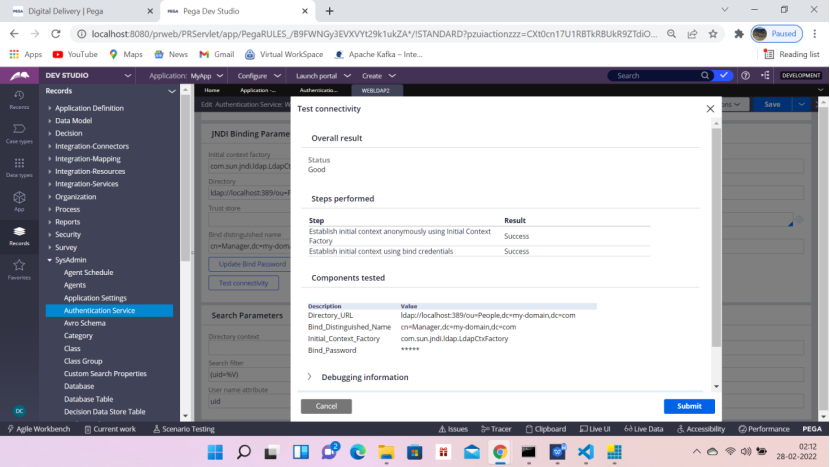
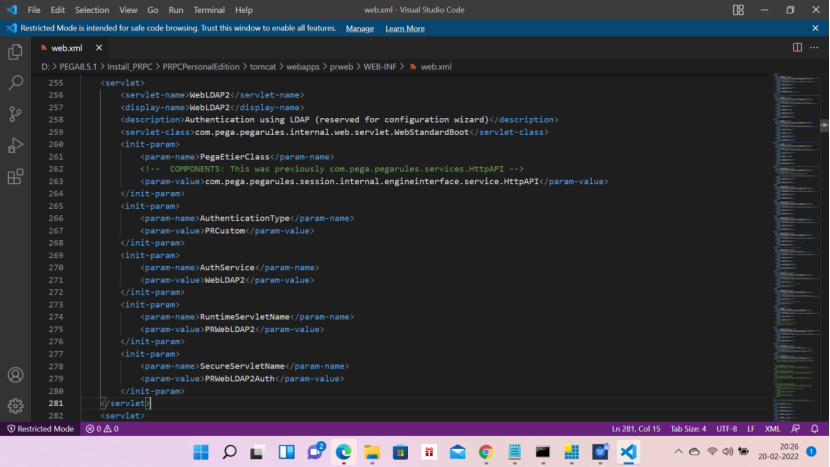
Now before clicking the Test connectivity, do the following check in the web.xml file in the below location.
D:\PEGA8.7\InstallPega87\PRPCPersonalEdition\tomcat\webapps\prweb\WEB-INF
Note: No change is required as the entry is already there
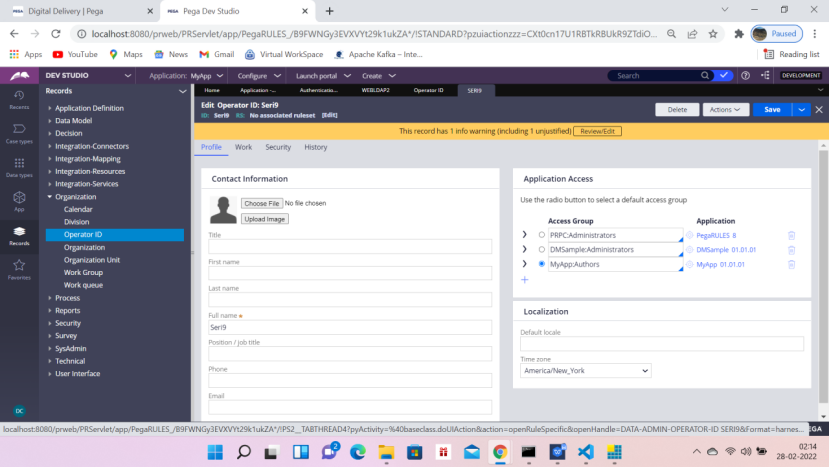
Now go to Pega and create an operator Seri9 / secret
Now type the following URL in incognito mode
http://localhost:8080/prweb/PRWebLDAP2
Use credentials
Seri9/secret
Then you should be able to login to Pega
This is the end of this article.
Whether you liked the article or not, please do let me know in the comment section
Please try it by yourself and if you face any issue then please let me know in comment.
I will definitely get back o you.
Happy Coding !!


Thanks for sharing. Got a clear idea.
Thanks Rajesh.
Well explained. Liked your blog. Please post more articles.
Thanks Priyanka
nice article.
Implementing SSO with third party identity provider and then LDAP pulling for additional info possible?
Hi Krishna, Thanks for visiting this blog.
Well, in the real world, companies buy some directory like LDAP to keep their employees’ data and then they want SSO on top of it.
This POC is about that.